Scam emails are getting harder to spot, and a new method uncovered by security experts shows just how far attackers are going to make their phishing attempts look legitimate.
A recent report from Bleeping Computer highlights a clever trick that makes fake Google and PayPal security alerts appear completely genuine, even passing official security checks.
A Clever Scam That Slips Past Security
Nick Johnson, a seasoned developer and lead for the Ethereum Name Service (ENS), recently received what appeared to be a real security alert from Google. It claimed that law enforcement had issued a subpoena requesting access to his Google account data.
Everything about the message looked authentic. It even landed in his inbox alongside real alerts from Google. The message was signed and delivered by Google itself, which made it all the more convincing.
So how did the scammer pull this off?
Using Google’s Own Tools Against You
The attacker hosted a fake login page on sites.google.com, which is a legitimate Google service that anyone can use to create web pages. Then, they used a trick to get Google to send them a real security email, which they later forwarded with their scam content included.
Since Google originally generated the email, it was properly signed with a valid DKIM (DomainKeys Identified Mail) key. This allowed the phishing email to pass through standard email security filters without raising any red flags.
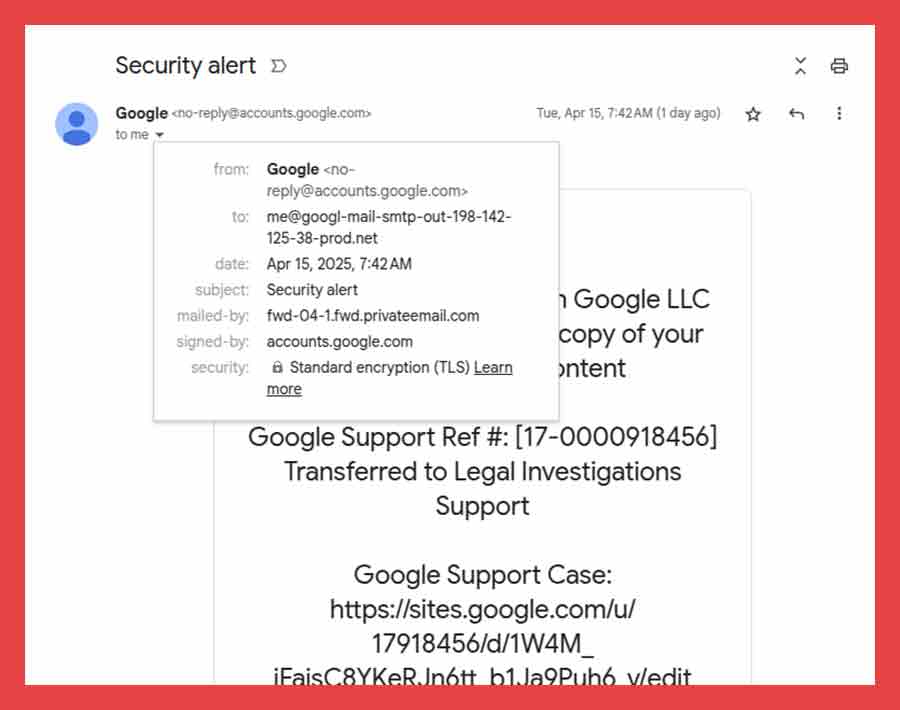
Even the sender’s address appeared to be [email protected], and Gmail displayed the message as if it were sent directly to the victim.
Why it Works
The issue lies in how Google’s systems handle DKIM verification. While DKIM checks the content and headers of the email, it does not verify the actual sending envelope. That leaves room for attackers to forward legitimate-looking emails that are technically still valid under these checks.
The fake login pages are near-perfect replicas of the real thing, designed to steal login credentials from unsuspecting users. Google is reportedly working on a fix, but for now, this method remains a risk.
PayPal Attacks Use Similar Tricks
A similar strategy has been used with PayPal back in March. Scammers exploit PayPal’s “gift” feature to make phishing messages look like they come from a real PayPal address. These emails can also include links to fake login pages meant to harvest account info.
How to Protect Yourself
The number one rule: never click on links in emails that ask you to log in, especially if the message feels urgent or alarming. Instead, go to the website directly by typing the URL or using a bookmark you trust.
Be extra cautious with emails that:
- Claim your account has been compromised
- Include invoices for things you didn’t buy, with a link to cancel
- Say you owe money for taxes or tolls and need to pay urgently
- Mention legal action or law enforcement subpoenas, urging you to respond
Even if the email looks completely legit, it’s always safer to verify by visiting the site directly or contacting support through official channels.






