Those little green and orange dots on your iPhone? They are supposed to be your digital bodyguards.
Since iOS 14, Apple has made a major privacy point out of its recording indicators. When the camera turns on, you see a green dot. When the microphone activates, you see an orange dot.
New research shows something important though. If your iPhone is already fully compromised at a deep system level, sophisticated spyware can hide those dots.
Before you panic, let’s break this down properly.
What the research actually found
Security researchers at Jamf discovered that Predator spyware can suppress iOS privacy indicators.
Predator is not some random App Store malware. It is classified as commercial spyware, typically used in targeted surveillance operations.
According to Jamf Threat Labs, once a device has already been compromised at the kernel level, Predator can:
- Inject code into SpringBoard, the system process that manages the home screen and status bar
- Intercept camera and microphone activity updates
- Block the signal before it reaches the interface
- Prevent the green or orange dot from appearing
Here is the unsettling part. The phone continues working completely normally. Apps launch, notifications arrive, and the interface behaves as expected.
You just do not see the dot.
How iOS normally protects you
Under normal conditions, apps cannot hide recording indicators. When the camera or microphone activates:
- iOS sends a system level notification
- SpringBoard receives it
- The status bar shows the indicator
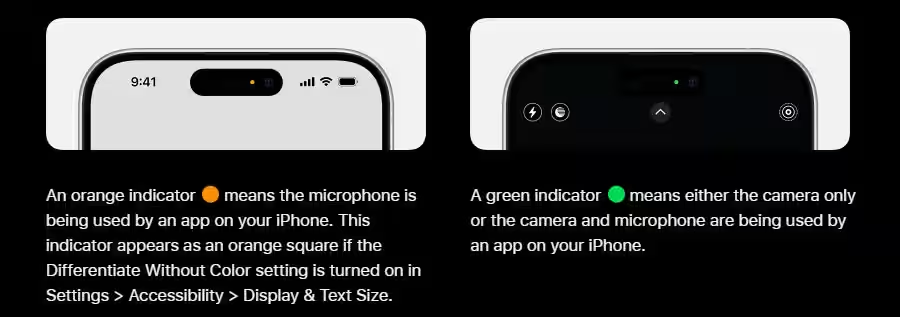
Apps do not control this process. That separation is intentional and designed to prevent exactly this type of abuse.
Predator bypasses the system by hooking into the internal method that handles sensor updates. In Objective C, if you send a message to a nil object, it is silently ignored. Predator exploits that behavior to discard the recording notification entirely.
One hook can suppress both indicators because iOS routes camera and microphone activity through the same internal pipeline.
SpringBoard never learns that recording began, so no dot appears.
This is not a new iPhone vulnerability
This research does not describe a new iOS flaw. It does not mean App Store apps can secretly record you, and no, it does not mean Apple’s privacy indicators are broken.
This only works after:
- Kernel level compromise
- Code injection into protected processes
- Deep system exploitation
In other words, if this is happening, your device was already seriously compromised. This is post compromise behavior, not a new entry method.
Who should actually worry?
Predator falls into the category of commercial spyware. That typically targets:
- Journalists
- Political figures
- Activists
- Executives
- Government officials
For the average iPhone user, Apple’s recording indicators still function exactly as designed.
What this research highlights is a broader security principle. Once an attacker controls the operating system at a deep level, even trusted interface signals can be manipulated.
That is not unique to Apple. It is a general reality of system level compromise.
How to protect yourself
If you want practical steps, focus on prevention.
Keep iOS updated
Apple regularly patches vulnerabilities used in advanced attack chains.
Restart your iPhone periodically
Some post exploitation frameworks rely on memory persistence. A reboot can disrupt certain footholds, even if it is not a guaranteed fix.
Watch for unusual signs
- Unknown configuration profiles
- Unrecognized VPNs
- Unexpected device management enrollment
- Repeated unexplained crashes
Use Lockdown Mode if you are high risk
Lockdown Mode significantly reduces the attack surface by limiting message attachments, web technologies, and wired connections.
If you are in a higher risk category, it is worth enabling.
The bigger takeaway
This does not mean your iPhone privacy dots are useless. It means that once a device is fully compromised at the kernel level, even system level trust signals can be altered.
For most users, the green and orange dots still do exactly what they are supposed to do.
If you want the full technical breakdown, including how Predator hooks into SpringBoard and suppresses sensor updates, the original Jamf Threat Labs research provides a much deeper look.
Sometimes the most important security stories are not about a new bug. They are about understanding what happens after a device is already under someone else’s control.





